In this tutorial, we will learn about AWS IoT Core. In AWS IoT there are different levels of services that could be used to define an IoT system. Especially, in this tutorial, we will focus on AWS IoT Core, as well as AWS IoT analytics.
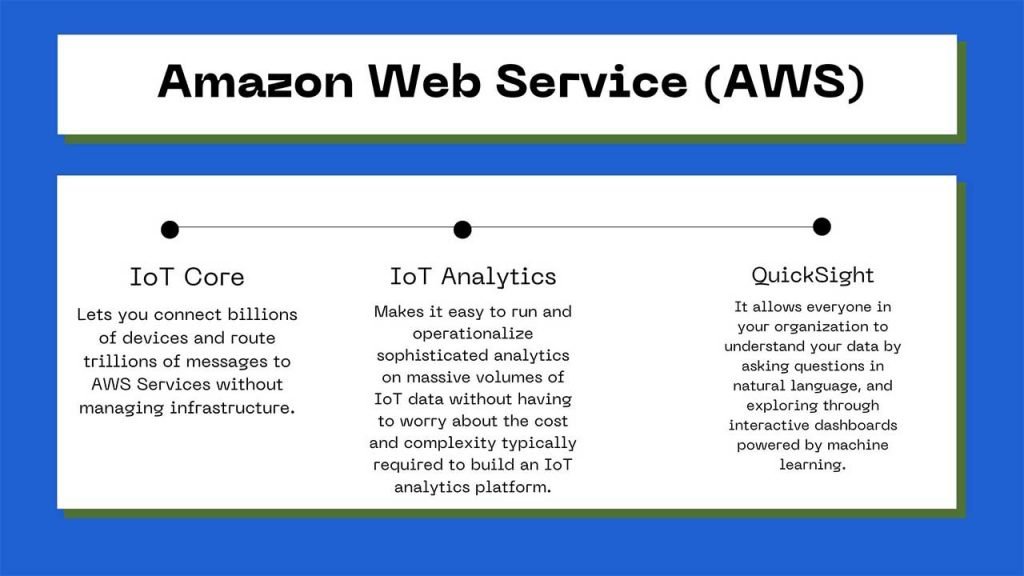
Furthermore, we talk about the type of services we’re going to use in the upcoming projects in order to define an AWS solution for our smart home products.
As I said we’re going to use IoT Core, IoT Analytics, and QuickSight in order to build IoT device communication with the cloud, perform analytics on the sensor data and use a dashboard to illustrate the final result of the analytics.
Order PCB From PCBWay
There are so many forums or communities for electronics online in today’s technical world, and one of the famous ones for PCB manufacturing is the PCBWay. PCBWay is a place that brings manufacturers and customers together. They have more than a decade of experience in this field of fabrication, prototyping, and assembling PCBs. PCBWay has proved its focus on its customers’ needs in terms of cost-effectiveness, delivery, and quality.
How PCB Manufacturing Process Done in PCBWay
Standard quality for any product needs to be maintained using some parameters. PCBWay gives that opportunity through quality control in designing and manufacturing. At first, they ensure the accuracy, clarity, and validity of the PCB files that we sent to them.
Then all the boards will go through the most stringent tests other than the basic visual check. They adopt most of the testing and inspecting equipment used in the industry, such as Flying Probe Tester, X-Ray Inspection Machine, and Automated Optical Inspection (AOI) Machine. PCBWay has 50+ new engineers on a daily basis around the world using PCBs for their work, who trust for their reliable quality. They produce high-quality pink, orange, grey, and even transparent solder mask. Moreover, according to people’s needs, they can also provide Black core PCB. Check it out for a High-Quality PCB solder mask. There are some pictures below of the new colors of solder musks.
Features of PCBWay
PCB Prototyping & Manufacturing: PCBWay produces FR-4 and Aluminum boards and advanced PCBs like Rogers, HDI, Flexible and Rigid-Flex boards, at a very reasonable price. Just check this Instant Quote to order premium PCBs for your hobby projects.
PCB Assembly: It not only offers PCB Prototyping but also offers PCB Assembly service. You can order a full PCB board with attached components by uploading your file. SMT & THT assembly starts from only 30$ including free stencil and worldwide shipping. The components can be sourced and provided by PCBWay, or by clients themselves.
Open Source Community: It not only offers PCB Prototype & Assembly service but also gives opportunities to students for sponsorships. I think this is so great. They feature their projects on the website also.
3D Printing & CNC: It also produces Rapid Prototyping like 3D printing, CNC Machining, Sheet Metal Fabrication, and Injection Molding. The quality of the product is too premium and reliable. And also the best part is that you will receive your order within a minimum of 3 days.
PCBWay Store: More boutique gift modules are waiting for you to discover, giving your creativity wings. You can order all types of electronic equipment, components, and many more with exciting offers. Go with the link and buy your needs, PCBWay Store.
Services: PCBWay offers great servicing of their products. According to courier service, it takes only 3 to 15 days to deliver your products. Also, it has a live support facility. Whenever you have any problems, you can always reach a live customer service person to respond to your emails.
How does AWS IoT Core Work?
Let’s focus on IoT Core. IoT Core allows you to connect billions of devices and trillions of messages in AWS service.
IoT Core works based on a publish and subscribe managing pattern, which is the same protocol that is used in MQTT.
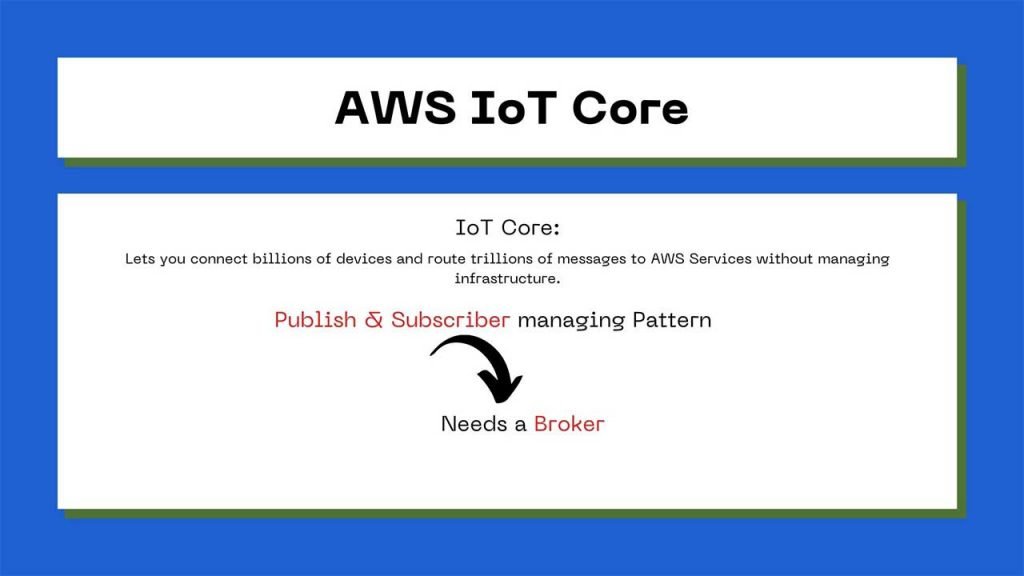
We already know that if you are using publish and subscribe managing partner or protocol, we would need a broker to allow the communication between the publisher and subscriber.
In the IoT core solution, There are three different types of protocols that allow such communication with the use of publish and subscribe, as well as a broker.
The three types of communication defining IoT Core are
- MQTT Protocol
- HTTPS and
- WebSocket.
So, in this lesson, we are going to use MQTT Protocol on AWS to perform the communication and connection between the microcontroller and the cloud.
AWS IoT Core Structure
Let’s talk about AWS’s IoT core structure. In this part, we want to introduce multiple parts definitions and structures that we will use during the tutorial.
Our goal here is to define and describe these terms. So when we work with them in the Tutorial, you are familiar with them.
Registry/Creating Things
One of these terms is the registry. Registry in AWS IoT core provides the identity for the device. It also allows us to track the metadata for each device.

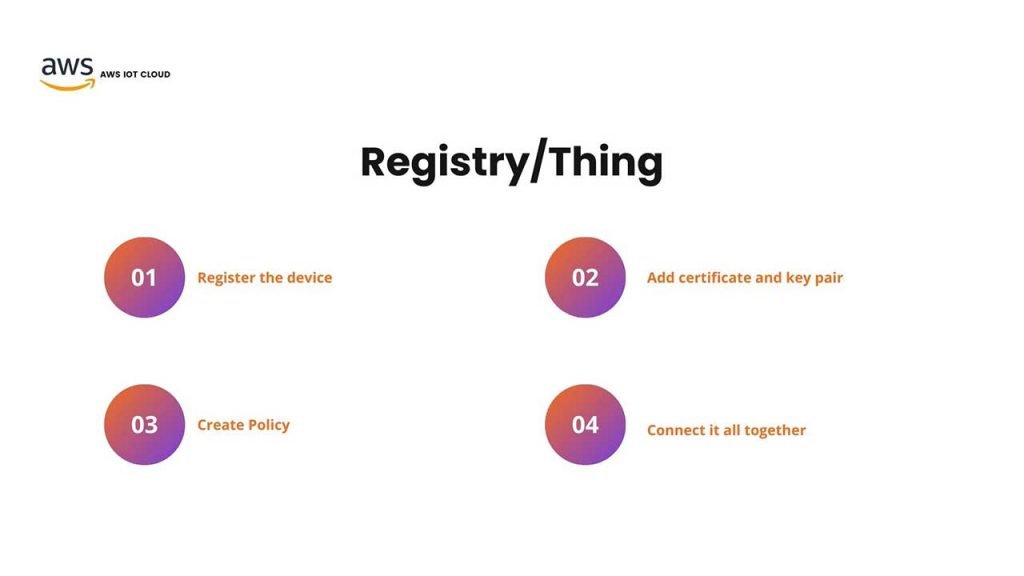
This means when we want to connect a device, let’s say an ESP32 or ESP8266 NodeMCU to AWS IoT core service. You’re going to register it. And by this registry, We’re assigning a unique identity for the device and we’re allowing that device to have metadata that we could track. In order to make the registry for a new device. There is a four-step process that we have to go through.
- First, we have to register the device on the AWS service.
- Next, we have to add a certificate and a key pair to make it encrypted and secure.
- Third, we have to create a policy, which describes how the device is going to be treated on an AWS and what kind of action that device can take.
- Lastly, we need to connect all these steps before together in order to fully register a device on the AWS cloud.
IoT Shadow
So as the first step, let’s talk about the registry of the device. As a part of registering a device on AWS IoT core, we have a concept called IoT Shadow.
IoT shadow essentially is the IoT device state. So in AWS IoT, when we talk about a shadow, we are talking about seeing the last state of the device and also being able to see the status of the device when the device is online and available during the build of AWS IoT devices.
If we want to use this shadow to see the last state of the device or set a new status for the online devices, we can use CLI or the command line. The shadow of the device is in a JavaScript format, so we have to have a little bit of understanding of JavaScript to be able to see and modify the status of the device.
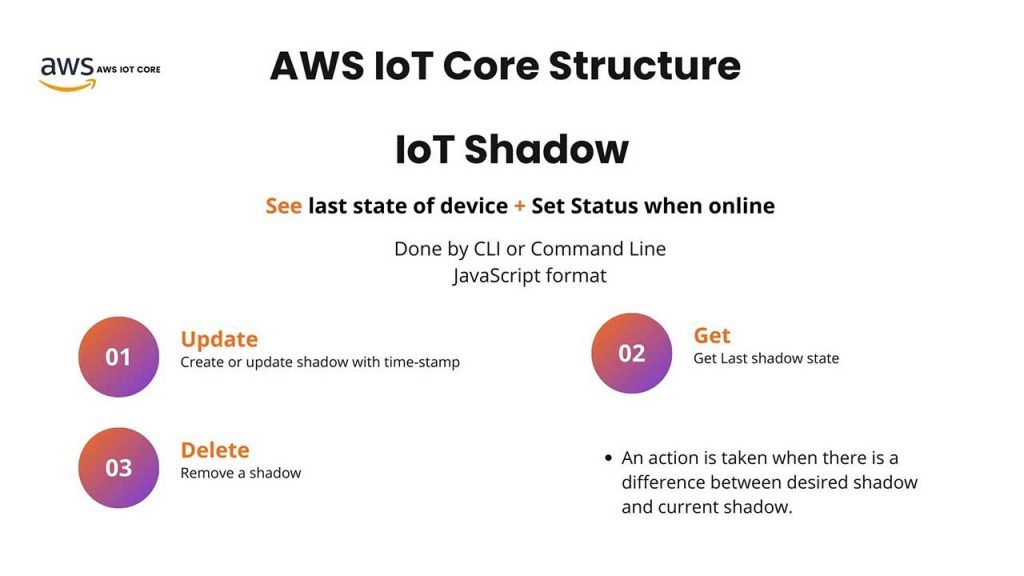
So there are three main things that we can do by use of IoT Shadow.
- First is an update. Updates create the device. And if the device already exists, updates actually update the shadow of the device with a timestamp of the update.
- Second, we can use a get in order to get the last shadow state.
- Lastly, we can use the Delete in order to remove a shadow from the AWS server.
It is worth mentioning one way that action would take place is when the desired shadow does not match the current shadow.
So there is that delta difference between the existing shadow and the desired shadow by the user. This will lead to a trigger of an action and therefore the change will happen.
Example of IoT Shadow
For example, let’s say in the smart home, you want to turn on a light with your phone.
When you press on a turn on lights on your phone, a shadow update is sent and it requires the device the light to have its state of on.

Because the existing shadow of the light is off, there is a difference between the desired shadow and the existing shadow.
This will lead to an action which is turning on the lights and then updating the shadow of the light to become on.
Add Certificate and Key Pair
So the next topic on the registry that we should talk about is adding certificates and key pairs. The idea behind using a certificate in specific X.509 is to encrypt and make the communication safe.
So first, it’s worth mentioning that this type of certificate is asymmetric or public-key cryptography.
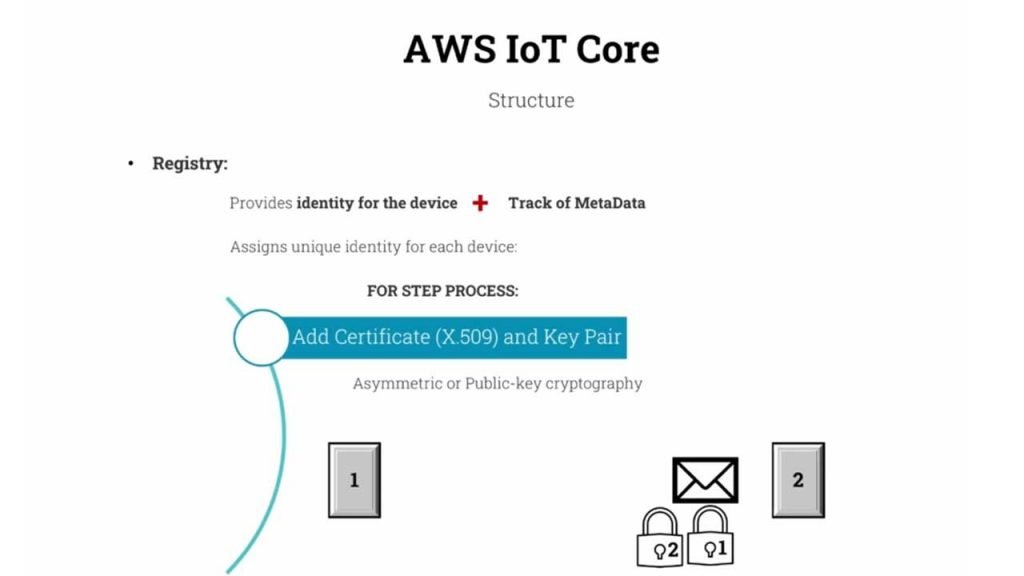
What this really means is that instead of having a lock on a device and sharing the password or the key to the lock between the two devices, we’re going to use a different way to lock and encrypt the information that we want to send. To better understand X.509 certificate.
Consider the following example.
Example of Asymmetric/Public-key cryptography
Let’s say we have two devices. Device number one and device number two. And we want to send a message from device number one to device number two.
In this type of cryptography, what we do is that we’re going to use a lock generated by device number one to lock the message. The only device that has the key to this lock is device number one. Device number one will send the message with the lock To device number two.
Note that it’s going to do this without sending the key to the lock. So device number two receives the message, but it’s been locked by device number one, and device number two does not know how to open the lock. At the next step, device number two is going to lock the message once again using its own lock.
So now we have a message and there are two locks on it. lock number one, which only device number one has the key to unlock. and lock number two, which only device number two has a key to unlock. Device number two, then send a message back to device number one. And now device number one has the original message with two locks on it.
Now in this step device number one, unlock the lock number one using the key that it had and the message will be left only with one lock that was generated by device number two.
Device number one is going to send a message back to the device number two.
And now the device number two has the message with a lock that knows how to unlock. and therefore by unlocking the device, it can read and understand the message. as you can see in this type of process.
We have the message being sent back and forth multiple times.
But the benefit is that the key is not shared between the two devices, so each device can have its own lock own key. And we are making sure that the message is secure.
Now that we have a better understanding about the registry of the device using Shadow to update the state of the device and how X.509 works.
Creating policy/IoT Rules
Now, we’re going to talk about creating a policy. In AWS IoT, core service. We have a definition known as IoT rules. IoT rules define how the device interacts with AWS services. The main parts of IoT rules are as follows.
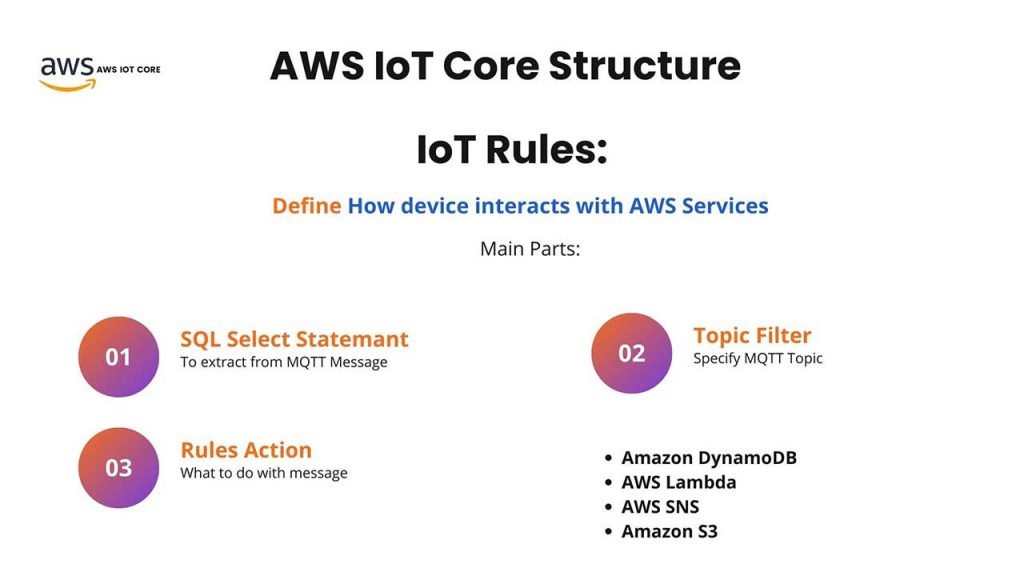
- First, we have a SQL select statement, which is meant to extract the information from the MQTT message.
- Next, we have a topic filter, which filters the MQTT message based on the topic and specifies the type of MQTT topics we want.
- Lastly, we have Rule action, which defines what to do when the message has arrived.
For this part, you can use many different services embedded within AWS such as AWS Lambda, Amazon S3, AWS SNS, etc.
Conclusion
Now that we have a better understanding about AWS. And we have covered different parts of the AWS IoT core. such as IoT Shadows, IoT rules, how to make this certificate, and so on. In the upcoming tutorial, we will implement AWS IoT Core and monitor the sensor data connected to ESP8266 or ESP32 Microcontroller from the AWS Service dashboard.